Lessons from Down Under's Data Disasters Pt. 3
We still need to talk about ransoms. And do some serious policy work about them.
Recap
This is the third in a five part series looking at the vast and varied implications of two major data breaches in Australia in the period September to November 2022.
The first post, which can be found here, covered the background to the two breaches at Optus, a major telecoms company, and Medibank, a health insurer which covers nearly 10 million of Australia’s 26 million population. It also discussed how our failure to distinguish between the severity of different types of data breach has bred a degree of complacency about data security.
The second post on the lessons of these incidents for Governments and their role in cyber security can be found here.
This third post analyses the issue of the the payment of ransoms.
The remaining posts in this series will cover:
how we discuss and report cyber harms, and why that matters (Part 4);
the safe haven problem in cyber crime (Part 5).
Lesson 3: sorry, but we still really need to talk about ransoms…
…whether it makes sense to pay, and, yes, whether it should be allowed
The Optus and Medibank data heists were accompanied by initial ransom demands of around ten million dollars.
Ten million dollars.
Yes, it was probably an opening pitch in a negotiation.
Yes, the Optus demand was apparently dropped, and Medibank, to their credit, didn’t pay.
But the fact that the demand was credibly set at ten million dollars shows we have normalised ransom payments, big and small.
In neither of these attacks was the actual operation of the company affected. In that respect, neither attack was even ‘proper’ ransomware as we have traditionally understood it.
These were threats to publish data, not cripple the operations of a company. Serious situations, for sure, particularly in the case of Medibank, given the sensitivity of personal medical records. But they weren’t the equivalent of, for example, the crisis in Irish healthcare in 2021, when the national system for allocating healthcare stopped working, with devastating results for patients.
And yet the demand for such a huge sum seemed normal.
That’s because it was.
Ransoms are the oxygen of cyber crime.
They have become the source of income for some of the most effective cyber criminals. Ransomware earnings go far beyond the potential for monetising stolen data on the dark web, the original digital age criminal business model.
In 2021 the British firm Elliptic traced $90 million of ransom payments to just one group - the Darkside group - in a nine month period. In December last year, a joint advisory from the FBI and the Cybersecurity and Infrastructure Security Agency said that the Cuba ransomware gang has extorted its way to more than $60 million, out of £145 million demanded from more than one hundred organisations.
Chris Krebs, CISA’s founding head, has set out three reasons why ransomware has emerged as the pre-eminent cyber threat of our our times. First, there is endemically weak security in Western organisations. Second, Russia (and some other countries, but primarily Russia) provide a safe haven for cyber criminals. Third, the criminals’ business model works.
Ransoms, along with low operating costs and low barriers to entry, are central to the criminal business model. And part of making that business model work (and these are my words, not those of Mr Krebs) is what I call a ‘pro-criminal narrative’ around ransoms. In other words, too many times organisations are told, through a variety of means, that the easiest or indeed only way out of the lonely and difficult crisis they face is to pay.
So victims do pay, and the vicious circle continues.
You can take the view that there’s nothing to be done about this (give or take a bit of chasing after cryptocurrency payments). And you may be right. It’s a hard problem.
But perhaps a better starting point is to accept that allowing mostly Russian-based computer thugs to extort payments on this scale from law abiding companies with impunity on an ongoing basis represents an epic failure of global public policy.
We might want to think harder about whether there is something we can do before giving up.
If, as the last piece in this series argued, cyber security is a much a policy, economic, social and legal problem as much as a computer network security one, then this is one of the hardest, but most important, policy challenges of all.
So we need to talk about ransoms. And then do some serious policy work.
Why ransomware works
Why does ransomware work for the criminals? Let’s take a look.
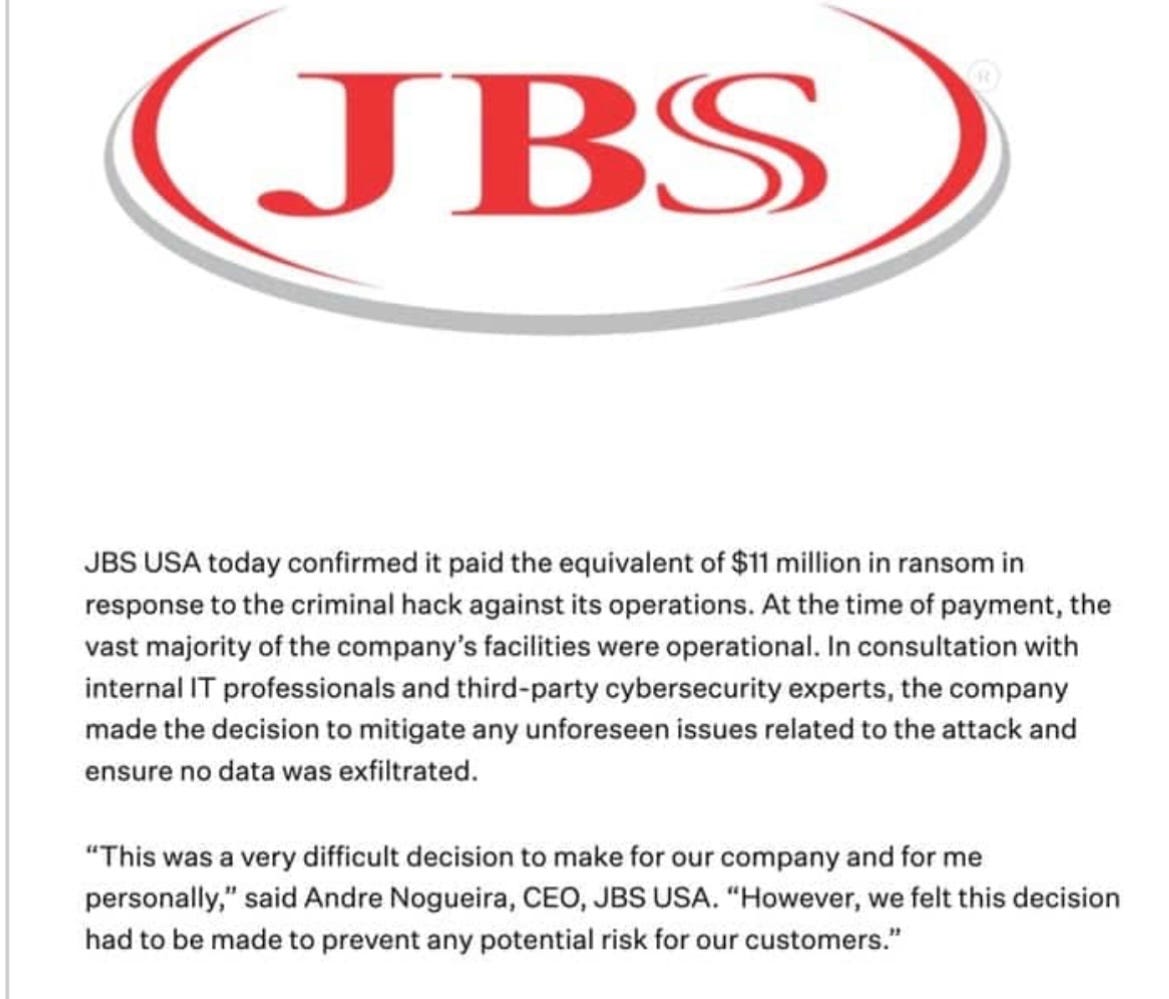
Below is the start of a statement by the meat giant JBS USA in June 2021. It is the main publicly available account from the company explaining why they paid $11 million - eleven million dollars - to the REvil group, one of the main Russian ransomware groups.
It merits careful reading.
The opening of JBS’s explanation of its 2021 decision to pay $11m in ransom
There are essentially two different problems to which paying a ransom is seen as the answer.
The first is to get systems that are not working to work by decrypting them. That is how ransomware has conventionally worked: the victim’s system doesn’t work as users are locked out, so the organisation cannot function. It must therefore buy a decryptor key to get back in to the network.
But in this case, JBS said that “at the time of payment, the vast majority of the company’s facilities were operational”.
The second reason, increasingly common (often alongside the first, though in the Medibank case it appeared on its own) is to prevent the publication of sensitive data. Essentially it’s “give us the money or we publish all your data”.
But in this case, the company says that the payment was made before data was exfiltrated, and indeed cites preventing the exfiltration (not publication) of data as a reason for paying.
The justification for paying eleven million dollars is “to mitigate any unforeseen issues” and “prevent potential harm to our customers”.
To be clear, JBS were perfectly entitled to take this entirely lawful decision. And, it may well have made sense to the company’s leaders for reasons they chose not to disclose. But, based only on the publicly available information the decision makes no sense (as a handful of people tried to point out at the time).
Moreover, note the intriguing reference to the advice of internal and third-party cybersecurity experts. Despite - if we take the company’s statement at face value - the absence of either disruption or data loss - the advice was to pay to make the problem go away. Again, this may have been perfectly reasonable to those with full knowledge of the case, though - again - it is not justified by the presentation of the facts alternatively.
But it is a powerful example of just how strong the incentives to pay are.
This is what I mean by a pro-criminal narrative.
If what happened at JBS happens at scale, continuously, then we’re stuffed.
JBS is perhaps an extreme example: in most of the known cases where victims pay there is a clear and obvious reason to pay. It’s either because the network is locked, or the criminals are threatening to publish data.
Still, it is apparent that in far too many cases the answer - however the advice is gathered and the decision is taken - is to pay.
Research presented today by at the SANS/UK National Cyber Security Centre Cyber Threat conference in London by Ifigenia Lella of the European Union’s cyber security agency ENISA disclosed that some 60 per cent of organisations paid the ransom in more than 600 cases analysed by the agency. This is the latest among a great deal of research about the prevalence of paying.
It is understandable. Victims of serious crime - which is generally committed from jurisdictions beyond the reach of domestic law enforcement - will want a way out of the problem as quickly and efficiently as possible. No one likes paying criminals, and no one should blame desperate victims for doing so. That’s especially the case when they’re told that the way out is to pay.
But this leaves us with the classic public policy problem where individual and collective interests collide.
What might make sense for individual entities is a recipe for serious collective harm.
That is a failure of public policy.
So are there different ways of doing things?
It doesn’t always have to be like this, and sometimes it isn’t
Not every organisation pays, and not every organisation suffers critical harm when they refuse to pay.
So it’s worth analysing some of the better known cases where victims chose not to pay, to see what we can learn. Here are three.
The Health Service Executive in Ireland, 2021
The first is the Irish healthcare system. Crippled by Conti ransomware in 2021, the Irish state faced numerous calls to pay in the light of the ‘double extortion’ problem - the severe damage to the provision of healthcare caused by being locked out of the system, combined with the threat of the disclosure of population level personal health data.
Eventually, the hackers backed down and provided the (only partially functional) decryptor key for free. (Why they did that is unknowable. Some ransomware operators steer clear of healthcare and abandon the operation when it becomes clear they’ve done over a hospital. In this case, speculation was rife that either the Kremlin and/or other ransomware operators were furious with Conti for engaging in such a venal attack so publicly, thus shining a light on this often quietly lucrative criminal enterprise).
What is interesting is not so much why the criminals backed down, but why the Irish Government held firm.
Even with the national healthcare system in crisis, the Government of the Irish State had to take the totality of the national interest into account. Had the decision been left solely to the affected body, the Health Services Executive, the incentives would surely have pointed towards paying. That’s why American hospitals pay all the time - their duty is only to their patients and their owners. But in Ireland, the decision was taken at whole of Government level, because the affected body was a public authority. The Irish State took the view that letting the world’s cyber criminals know that the Irish Government paid up carried even greater risks overall than those they were already facing with the crisis in healthcare.
Moreover, the full resources of the state could be directed at pace to support the stricken service. Irish Defence Force experts and American commercial expertise were swiftly brought in as the state threw the kitchen sink at the problem.
In the 2020s it has become increasingly common to talk of ransomware as a national security threat, at least when it comes to operations against critical infrastructure. But for the most part, Governments leave the absolutely critical decision on whether or not to pay entirely to the affected organisation. Colonial Pipeline is a good example of that; the American company shut down its pipeline which provides much of the East Coast’s gasoline and paid the ransom, leaving the federal Government to invoke emergency procedures to ensure supply, but the recovery up to the company.
Letting companies pay and leaving them to recover is, of course, entirely consistent with their status as private entities. But, when the incident has consequences which could be regarded as meeting the threshold of national security - as it surely is when energy supplies or healthcare is compromised - it is not consistent with treating ransomware as a national security threat. It is subcontracting one of the most critical decisions - whether or not to pay the attacker - to a private entity.
Put it this way, if someone bombed a pipeline, it would be seen as a national security issue for the Government to lead on. Why is shutting down the pipeline via a cyber operation different? If a hospital is stopped from functioning, should it really depend on how it happened to determine who is responsible for the response?
Ireland is an easy an example to focus on because the victim organisation was a public authority and therefore the Health Services Executive had no choice but to follow the decision of the Government not to pay. It is obviously much more complicated when the victims is a private company, even if it is providing a vital public service.
But Governments should think of the problem like this. If the decision to pay is left entirely in the hands of a single private entity, expect that entity to consider only its own interests, imperatives and duties. Do not expect the private company - voluntarily, without legal compulsion - to evaluate the wider public interest at the expense of its own priorities. That would be wholly unreasonable.
In other words, if policy doesn’t change, expect your critical national infrastructure companies to pay ransoms, at least some of the time.
And, consequently, expect the criminals to come back for more.
And, consequently, expect more critical services disruption from ransomware.
The Harris Federation of Schools in London, 2021
A different example involves the Harris Federation of some 50 London schools, ransomwared in April 2021. It, too, is instructive, but for a different reason. And a fascinating overview of it, courtesy of BBC Radio, can be found here (a 30 minute listen).
Throughout the attack, the Federation’s schools remained largely operational, though there were some impacts (for example, at one school, Internet-controlled gates would not open and had to be manually over-ridden). But the organisation was nonetheless badly affected, being unable to pay invoices, for example.
The initial ransom demand came in at $4million. This was completely unaffordable for Harris, which is a charity. Professional negotiators managed to get the demand down to south of $1 million.
But the organisation still decided not to pay. It looked coolly at the situation. Its main educational mission was continuing because that did not depend completely on the network. The computer network was already very badly damaged and would take time and money to recover, even with a decryptor key. Harris were cognisant of advice that not all decryptor keys work perfectly, and about 5 per cent don’t work at all. They knew there were other ways to recover.
So they held firm. Eventually, they calculated the cost of recovery at around $600,000; cheaper than the final ransom demand of $750,000.
It is not always cheaper and easier to pay.
The Medibank breach in Australia
This brings us to the Medibank case in Australia.
It is not hard to see that paying the ransom looked like an attractive option to Medibanks’s leaders, given public concern at the potential exposure of nearly ten million private medical records.
But, as the company presumably realised, extortion based on denying the availability of service and extortion based on the breaching the confidentiality of data are two completely different things. In the case of the former, the attacker can continue to lock out the victim, causing ongoing disruption. And the attacker has a clear ‘product’ to sell: the decryptor key. So there is a clear and obvious transaction to make.
In the case of extortion based on threatening to breach confidentiality through a data dump, this is not the case. Rather that a ‘positive’ action in return for money - the provision of the key - the victim is attempting to pay for a ‘negative’ action: not disclosing data, in perpetuity. ‘Guarantees’ that stolen data has been deleted cannot be verified.
As the cyber security firm Coveware put it in a 2020 study showing that some victims who had paid had seen either data released anyway, or had a further extortion demand levied later on:
“once a victim receives a decryption key, it can’t be taken away and does not degrade with time. With stolen data, a threat actor can return for a second payment at any point in the future.”
Furthermore, the dynamic is different in such cases because the network is still functional. Medibank may have been plunged into a serious crisis but, unlike the Irish Health Services Executive, its ability to arrange healthcare for its customers was unaffected.
Finally, as ever, the victim and wider society has agency in how it responds. As the next post in this series will explore, Australia handled the disclosure of medical data as threatened by the attacker deftly. A grown up conversation between the Government, the company, the media and socia media ensured responsible reporting of the leak, containing the harm to individuals and blunting the severity of the disclosure threat from the criminals. In both Ireland and Australia, public fears that personal health data would be easily available did not materialise.
Three cases, two lessons
Not for the first time in cyber security, details matter. Setting even legality and ethics aside, and focussing just on the practicalities and business realities of the situation, in both the Harris Federation and Medibank cases, it made sense not to pay the ransom.
Two separate questions arise from these three cases:
Question 1: the law. What should the law be around paying ransoms? Should payments remain legal, and who should take the decisions on paying?
Question 2: the narrative. Assuming that, at least for now, paying ransoms remains legal, how can we reduce the incentives to pay?
Question 1: The law
Whether or ransomware payments should be prohibited has been one of the most vexed issues in contemporary cyber security policy.
The Ransomware Task force - a US led group of international experts spanning the public and private sectors - conspicuously failed to agree on this topic amidst a welter of unanimous, useful recommendations. This is not to criticise them: it’s an enormously complex and contentious subject, and to their considerable credit they set out (at page 49 of their report) a balanced account of the debate on both sides. Indeed this published, accessible, and reasonable analysis, based on expert input, is more than any Government I know of has produced on the subject.
The UK Government has said nothing discernible at Ministerial level on the subject. This is in marked contrast to the British state’s robust, two-decade long policy on banning ransom payments to designated terrorist organisations for kidnaps via primary legislation with extra-territorial effect. Terrorism and cyber extortion are two very different issues, but the UK Government has not said why it takes such different approaches to the two when it comes to ransoms.
The US’s position appears to be that ransom payments are legal, unless they are paid to groups designated under the Office of Financial Assets Control (OFAC). Some individual hackers and well-known cyber threat groups are designated under OFAC, and so in theory paying them is illegal. However, many cyber criminal groups are not covered. And for those that are, extensive mitigations are set out in the US Government’s guidance. Moreover, as Recorded Future have set out, knowing whether or not criminals demanding ransoms are on a sanctions list is beyond many smaller organisations. RF’s report estimated that 15 per cent of payers in 2020 may well have breached US Treasury rules by paying ransoms. So it is hard to see the logic of these rules, or how they can effectively be enforced.
For most of the rest of the western world, the policy on ransom payments is not to have a policy. More than that, it’s not to even think about having a policy.
It’s a hard question, for sure. So it’s understandable that Governments want to duck it. But if they do, they should expect nothing to change.
In July 2021, the American cyber security expert Tarah Wheeler and I tried to set out an analytical framework for thinking about the law on ransoms from initially opposing perspectives (she instinctively opposing prohibition of payments, me instinctively favouring it).
We agreed that a simple outright ban with no mitigations would likely prove a disaster. To have a chance of being workable, a ban would have to be accompanied by significant guarantees of support, probably from the state, to be effective.
We also looked at the misalignment of incentives, responsibilities and information that encourage so many to pay.
Our conclusion was this:
“if a ban on ransom payments is to be a credible part of a strategy to stop the flow of money to such criminals, then surely an essential precondition is more effective state intervention in the response to attacks, reflecting the gravity of the problem as a national security threat”.
Having set out how such interventions might be developed and tested, we continued:
“Whether or not payments are banned, a more activist approach is needed anyway, even if it means legislating for more interventionist levers over privately-owned critical infrastructure.”
A huge part of the ransomware problem relates to policy. The reasons why it’s outstripped other forms of cyber harms are not technical or operational: they’re about the business model.
To go back to Chris Krebs’s triplet, countering ransomware means taking on the criminal groups operationally, improving cyber security at home, and also breaking the business model.
And this last part needs policy solutions.
Policy is normally formulated at least in part via the gathering of evidence, and formal expert consultation.
Yet Governments, when they comment at all, usually say simply that a ban on ransom payments won’t work. But no Government (to my knowledge) has tested the proposition properly through any recognisable, publicly disclosed policy evaluation process.
Some of the arguments against a ban are very powerful (threat to life situations in healthcare, for example, and the perverse outcomes that would arise from exempting the healthcare sector). But others do not bear up to scrutiny.
For example, one common argument against a ban is that it would drive payments underground. As Troy Hunt, the Australian cyber security expert, has argued, this is essentially saying that company directors would knowingly and willingly break the criminal law. There is absolutely no evidence to support this claim: plenty of company directors dislike the EU’s General Data Protection Regulation but that doesn’t mean they’ll consciously ignore their reporting requirements under pain of prosecution.
Furthermore, whether a ban is workable or not, policies on responding to ransomware incidents need further development. Specifically, returning to the lessons of the Irish and American healthcare examples, what is the balance between the public and private sectors when public safety is endangered by the compromise of a private entity? Should companies in critically important (and therefore already heavily regulated) sectors have a duty to report breaches? Is there a case for going even further and requiring them to consult, or even seek the consent, of the Government before paying? And if not, aren’t we just privatising national security risk?
This is complex, contentious stuff. The point is that all of the arguments for and against a ban, and other policy measures need to be tested in a formal process of policy evaluation and consultation.
What we have at the moment on the ransomware business model - and ransoms in particular - is policy inertia, justified by assertion.
Question 2: The narrative
That’s not good enough, but it is where we are.
Therefore, given the ransom policy inertia in most capitals, it is a prudent assumption that in the short term at least, the legal position in most countries will remain as it is.
Therefore, Governments, along with the wider cyber security community, must work harder to change the pro-criminal narrative that paying is often the best option.
It is easy for public authorities to ‘advise’ companies not to pay. That advice is genuine but, to a company in serious crisis, it is often meaningless. Governments understand this, and sometimes the don’t pay ‘advice’ is accompanied by thoughtful nods indicating that the authorities understand if the organisation takes the ‘wrong’ decision.
That is why stories like the Harris Federation’s gloriously stubborn refusal to pay - and saving money in the process - are so important. It is why understanding that extortion for availability and extortion for data protection are completely different things is so important. It’s why the Barracuda research that 80 per cent of organisations who paid got hit again is so important. It’s why research such as that by Hiscox Insurance, which shows that 29 per cent of victims of data extortion who paid up still had some data leaked is so important.
It’s also why the national dialogue in Australia about how to report and discuss the Medibank fiasco responsibly is so important (the subject of the next post in this series in two week’s time).
We have to shift the pro-criminal narrative.
Conclusions: the case for a substantive, inclusive, expert policy review
A holistic approach to ransomware will bring together operational and policy measures across like-minded allied nations.
President Biden’s 30 nation strong counter-ransomware group has announced a range of operational activity to try to mitigate ransomware. These measures absolutely have their place and we must hope they make the desired breakthroughs.
But ransomware is as much of a policy problem as it is an operational one, if not more so.
Yet when it comes to policy, Governments are mostly asserting that policy changes won’t work. But they’re doing that without engaging in the normal process of expert engagement, evidence gathering, and evaluation of options.
They are vindicating the age-old bureaucratic saw that doing nothing is always an option.
The case for substantial policy and legal changes to counter ransomware is not yet made. But nor is the case for dismissing the options without carefully examining them. There is a compelling case in many countries for a substantive, open-minded, consultative policy review of counter-ransomware policy options. This should be debated, published, and then - depending on the outcome - action should follow.
And in the meantime, there is a compelling case for a renewed effort to shift the narrative away from the criminals.
By telling the stories that show that paying doesn’t always pay.
We can and must do better.
Coming up next in the series
The fourth part in this series, on the way Australia managed the disclosure of data in the Medibank breach, will be published in early March.
In the meantime, there may be one or two other posts on other subjects on this Substack page.



Perhaps a focus on backups, and funding for the infrastructure for resilience would be worthwhile ?
Board and it requirements for ensuring that things work, demonstrating that resilience is successfully engineered for, and funded against the competing priorities for the organisational funding.
Events show that organisations need IT infrastrucure that has appropriately funded budgets, do that they are not hampered with legacy vulnerable systems & software within their organisations that can be exploited and monetised.
How will the transformational investment be found to get from where we are to the future, against every othe funding priority?
Here be dragons.